As the risk of being targeted by cyberattacks is steadily increasing, prevention and defense against them are mandatory in every organization. The origin of the three lines of defense model as a concept to holistically manage risks lies in the financial sector and regulators and consultants often recommend it. Thus, many organizations in the financial industry around the globe started following this approach. The model aims at providing efficient and effective risk management, not just regarding cyberattacks. In the context of cybersecurity, the three lines of defense can be adopted to handle emerging threats and the associated risks.
We aim to give a concise overview of the Three-Lines-Of-Defense model as a starting point for more in-depth content where we will take a closer look at its limitations and challenges when implementing the model into the organization.
What are the benefits of the Three-Lines-Of-Defense model?
First of all, it is easy to understand, and it provides a clear focus on what is essential by using a clear description of critical functions concerning risk management and control. Another critical point is the overall coverage of key risks because the three lines of defense approach allows finding gaps in assurance more easily. Moreover, this also helps reduce the unnecessary duplication of coverage, thus reducing the assurance activities’ cost.
Implementing Three-Lines-Of-Defense is not the same for every organization
Although many organizations adopted the three lines of defense, and there is a consensus that the model offers a good governance structure, the model only provides a general description. This means the implementation details can differ from organization to organization, and thus there is room for confusion and debate on how exactly the model should be used.
Where did the model come from?
This model is not an entirely new concept. The first occurrences of the three lines of defense actually go back to the 1990s. However, it was first introduced to a broader scale by the Basel Committee of Banking Supervision in 2011, followed by the Institute of Internal Auditors in a position paper in 2013. This led to wide-ranging adoption in the financial services industry.
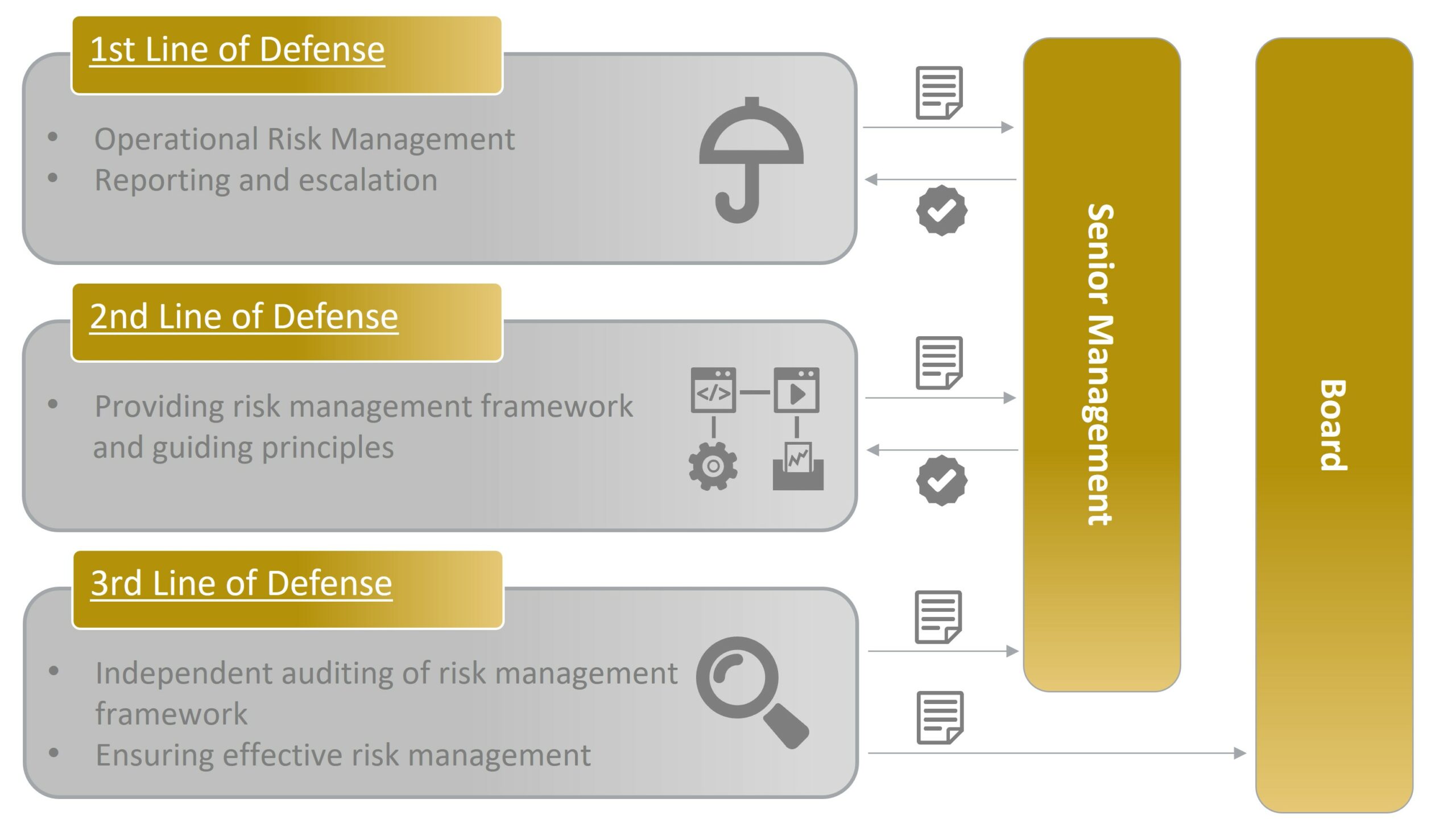
Figure 1: The three lines of defense model
First line of defense
The first line of defense consists of the operational managers, such as product owners, who own and manage risks. They are responsible for implementing preventive, detective and corrective controls suitable for operational risks. They also need to ensure that there are procedures following the policies set by the second line. Therefore, the first line of defense is responsible for creating these procedures, aligning them with the second line of defense, training users and confirming that employees comply with the procedures. They ensure the effectiveness of the risk management using internal controls and report to senior management.
Second line of defense
The second line of defense often consists of the IT risk management and IT compliance functions. Its main function is to provide the framework for effective risk management through guidelines and policies. The second line oversees and monitors the activities of the first line concerning their conformity with the framework. The monitoring and the overseeing functions ensure that the controls are well designed and operating effectively. They also report to senior management. In practice, the second line of defense is torn in two directions. It spends a lot of time and effort enabling the first line to properly implement the controls as designed while simultaneously negotiating the framework with the third line. A key to a successful 3-LoD implementation is to place the 2nd line of defense where it has enough access to the first line while remaining independent and in touch with internal auditors.
Third line of defense
The third line of defense provides independent assurance that the first and second lines of defense function adequately and effectively. While the second line of defense monitors whether the controls applied by the first line are effective within the provided framework, the third line verifies whether the used framework fully covers the operational or legal risks. Therefore, it consists of the Audit function overseeing the first two lines. Internal Auditors and/or external Auditors can be used to confirm governance and compliance effectiveness and help with further improvements. They report to both senior management as well as the board.
What does it mean for IT security?
Adapting the Three-Lines-Of-Defense model for handling cybersecurity risk usually leads to the second line implementing high-level policies (e.g. based on international standards like ISO 27002) and maintaining a risk dashboard while the first line is in charge of procedures and technical security measures. The actions performed by the third line do not differ drastically from other applications of the model.
Since the distinction between second-line activities and first-line responsibilities is not always clear when handling security risks, additional communication efforts are required to ensure adequate and efficient management of these risks. This intersection of responsibilities can also be seen in publications like NIST Special Publication 800-53 and BSI Grundschutz, where both controls implemented in the second line and controls implemented in the first line are present.


Recent Comments