When it comes to security concepts, there are several measurements that one should keep in mind. The most common and primary goals of a security infrastructure are the goals of the CIA Triad.
The CIA Triad is an information security model that is used to create a security policy. This model has a rich history, dating back to its use in 1998. The security of information does not only relate to cybersecurity but applies to scenarios such as filing and record storage as well.
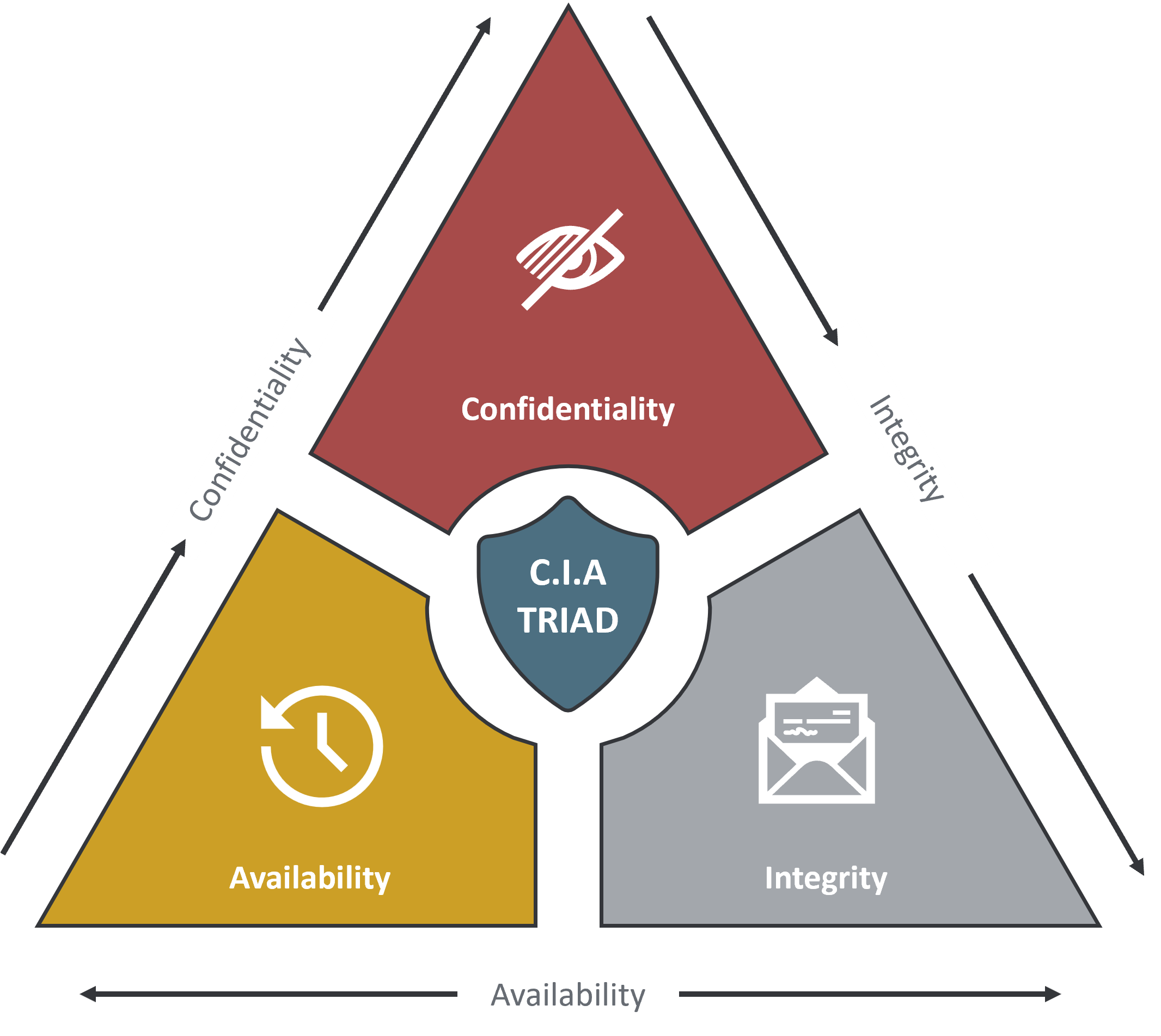
Figure 1: The CIA Triad overview
The CIA Triad consists of three sections:
- Confidentiality,
- Integrity and
- Availability
This model has quickly become an industry standard today. The model should help determine the value of data and the attention it requires from the business.
Unlike traditional models, the CIA Triad operates as a continuous cycle. Although the three elements of the triad can overlap, the failure to meet even one of these elements renders the other two ineffective. Any security policy that neglects these three sections is unlikely to be effective.
These three sections are also the basis of information security, which aims to prevent the loss of availability, integrity, and confidentiality for systems and data.
Confidentiality
The focus of this concept is to avoid and protect sharing information with individuals who lack proper authorization and misuse it. Organizations always have some form of sensitive data stored on their systems and must do everything to ensure their data is protected and private.
An adequate system ensures that only those authorized to access the data have the necessary privileges.
Integrity
The element of integrity in the CIA Triad is the condition that information is kept accurate and consistent unless authorized changes are made. The information can change due to careless access and use, errors in the information system, or unauthorized access and use.
Integrity is maintained when the information remains unchanged during storage, transmission, and usage without altering the information. Steps must be taken to ensure that unauthorized people cannot modify data. Access control and rigorous authentication can help prevent users from making unauthorized changes. Hash verifications and digital signatures can help ensure that transactions are authentic and that files have not been modified or corrupted.
Availability
For data to be useful, it must be available and accessible by authorized users. The main concern in the CIA Triad is that the information should be available when authorized users need access.
Availability is a key benchmark for an organization, and having 99.99% uptime on their websites or systems is often laid out in Service Level Agreements. When a system is unavailable, it can damage an organization’s reputation and finances. Availability is achieved through a combination of reliable and well-tested hardware for information technology servers, redundant technology and services in case of primary failure, and implementing well-versed security protocols to protect technology and services from attack.
The CIA Triad offers a straightforward yet inclusive high-level checklist for evaluating security protocols and technologies. A system that satisfies all three sections is considered effective.

Recent Comments