Social Media Monitoring is used in cybersecurity to detect and prevent threats from social media or other social interaction channels like forums or chatrooms. This should not be confused with social media intelligence which sounds similar but is an entirely different method used in marketing to analyze the behavior trends of individuals from social networking sites.
What is Social Media Monitoring?
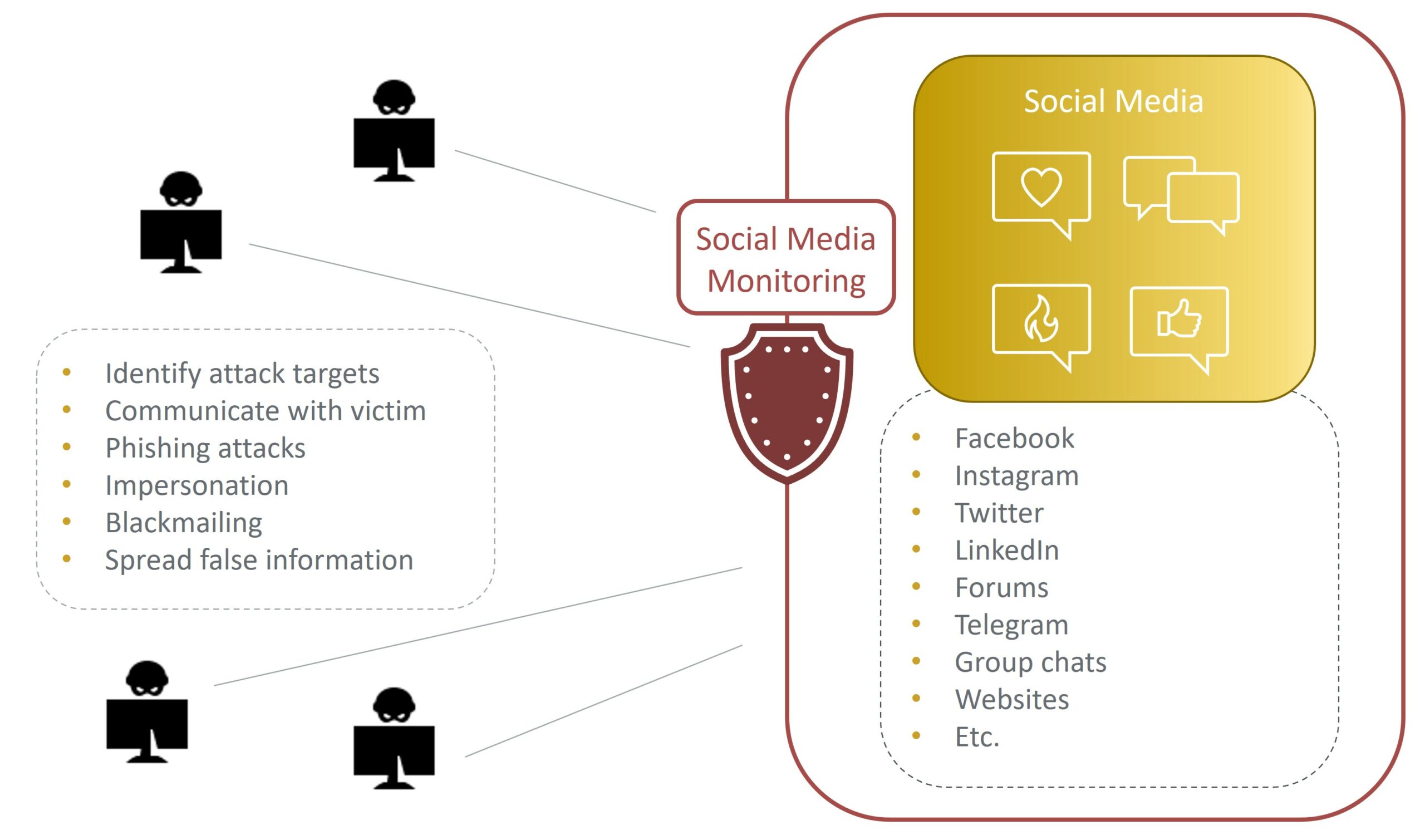
Today’s criminals have also learned about the power of social media. Information about a user can easily be looked up through posts and profiles, making phishing attacks more effective or even encouraging blackmailing. To counter this, Social Media Monitoring tries to identify possible attack vectors and threats by analyzing written posts, comments, and even articles. There are also some cooperation’s with intelligence services, which monitor potential aggressors of important events and other targets which need surveillance. Social Media Monitoring can not only observe the publicly available information such as online profiles or status posts but also non-public or private information such as private forums or Telegram channels. However, there are also limitations to this, as privacy protection does not allow for monitoring private channels without the consent of the users.
Figure 1: Social Media Monitoring Overview
Why should it be used?
There are multiple reasons why you want to use social media monitoring. An attacker might discuss potential targets with other criminals on the internet, and thus Social Media Monitoring can help identify the attackers and their targets. Furthermore, accidental data leaks like sharing sensitive information on social media or data leaks from actual hacking attacks can be found efficiently and thus timely deleted. It can also identify the spreading of false information and thus allows for a quick response to mitigate reputational damage.
Challenges of Social Media Monitoring:
The amount of data posted every second on social media platforms is enormous, and most of it is perfectly fine and not related to cyber-attacks. Therefore, it is challenging to find the relevant information and filter the other noise. Machine learning algorithms help to differentiate this noise. But not all problems can be solved with machine learning, as there are some limitations related to the privacy protection laws, as private channels are not open to being monitored by private companies. Even publicly available information can be declared private according to Article 8 of the European Convention on Human Rights, and thus the legal boundaries have to be checked beforehand.
Conclusion
Social Media Monitoring can provide valuable information on threats and possible targets, but on its own is not enough to provide a complete knowledge base on potential threats. The best way to incorporate Social Media Monitoring is in a holistic risk management approach as a complementary source of information.


Recent Comments