The explosive data growth in recent years causes companies to lose track of the information coming in and out of business. Businesses worldwide report that at least half of their company data is dark data, i.e., untapped, unused, or completely unknown. This situation leads to serious security gaps where companies can become victims of cyber-attacks. SIEM (Security Information and Event Management) can perform log aggregation & monitoring, such as the market leader in the field Splunk.
The SIEM solutions analyze machine data to deliver operational intelligence for security, IT, and the business. This can help a company attain a holistic view of all its data and allows the company to regain control of its data. Data can be imported from any structured or unstructured source in the company’s system and monitored and analysed in real-time. Automatic notifications with alerts and reports can be configured and sent directly to the security team when an incident occurs. This enables security departments to react quickly to threats according to their prioritization.
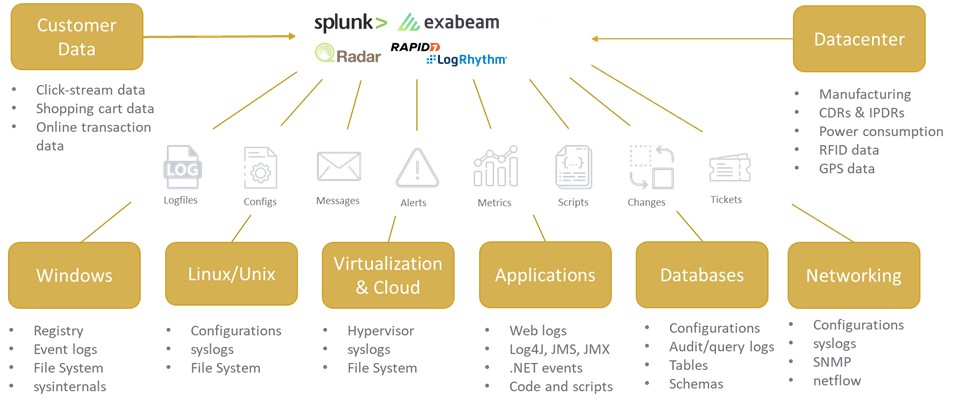
Figure 1: Log data management solutions have the capabilities to receive Log-data from numerous data sources in an organization.
The SIEM solution acts as a log data consolidation and reporting engine, capturing essential security-related log data from devices and software, such as networks data, phishing prevention, firewalls, and user management and behaviour. A Dashboard can generate insights and visibility, calculates risk scores, and identifies threat and anomalies from the entire network. The SIEM Solution can perform Correlation analysis an all its data that is collected through Aggregation. SIEM looks for similarities, repeating occurrences, and patterns of the log data. System administrators can better notice repeated breaches, attempted breaches, trends toward failure, and other recurring or escalating incidents. Valuable manpower can be saved as all of this is automated and can minimize the down time in the event of an incident.
If your organization is looking to implement a SIEM solution or want to expand their existing instance, contact us. Our Cybersecurity Experts will identify your gaps and light the way of closing them.


Recent Comments