Due to digitalization, the number of cyberattacks will inevitably increase worldwide, as the possible attack vectors that a potential hacker can exploit increase proportionally to the increasing connectivity of systems. The consequence of this is that the system needs for cybersecurity and data protection increases to protect from these threats.
There is never a guarantee of preventing a threat in cybersecurity and data protection, but there is a clear goal to minimize cybersecurity risks. Whether for an IT infrastructure, cloud-based services, or an embedded connected device, the first step is always to analyze the possible risks to work towards risk minimization. This analysis takes place in a so-called cybersecurity risk assessment.
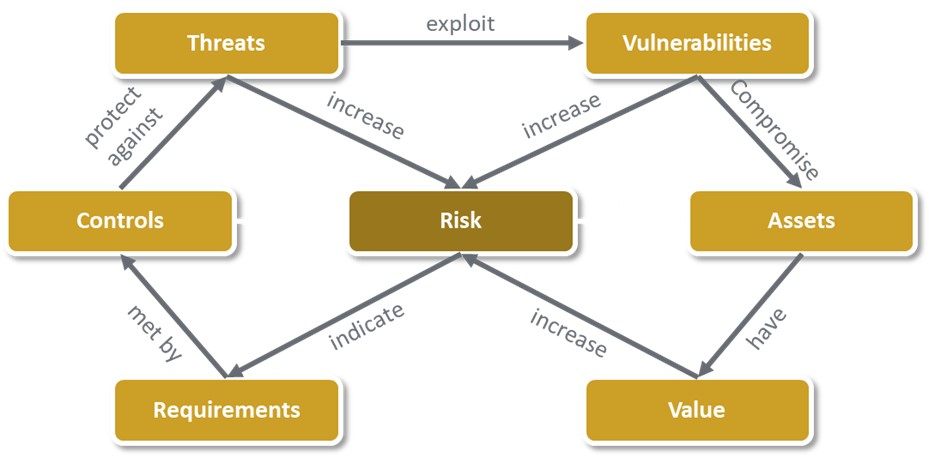
Risk assessments are about identifying all assets worth protecting to analyze all threats possibly affecting the asset. Without a structured approach, threats and vulnerabilities will likely be overlooked in the long run, which attackers can easily exploit to cause damage. The possible effects of such an attack are manifold: Very high financial costs can arise if, for example, systems are no longer accessible for a more extended time. Manipulation and theft of data can cause direct damage to the end-users of the system, resulting not only in financial damage but also in significant damage to the company’s reputation. A risk-based approach is therefore not only required by law but is also in the company’s own financial interest.
Figure 1: How risks arise at what influences them
At Ginkgo, we use a holistic, top-down attack-tree-based approach that ensures high quality and at the same time allows us to work as efficiently as possible. This Ginkgo approach achieves the following three benefits:
- completeness: a structured process with high traceability requirements is necessary to ensure that all threats are covered. Of course, a risk analysis will never identify all existing vulnerabilities, but the highest possible coverage is essential to mitigate all risks successfully.
- reusability: Comparable attack paths can endanger various assets or result in additional damage scenarios. Referencing attack paths is the key to avoid errors and unnecessary effort. This is also true for controls that can be referenced for multiple assets. Referencing can also be used for similar systems across numerous projects to minimize effort and create consistency.
- compliance: The quality of risk analysis must be measured against appropriate standards. To prove that our process is state of the art, we implement recommendations and requirements from security standards ISO 27005, ISO 15408, and, especially for the automotive sector, ISO 21434 in our own risk assessment process.


Recent Comments