Compliance with the provisions of the GDPR has been binding since May 2018. It seemed that the draconian penalties threatened for violations would not be pronounced in practice in the first months and years. That has changed in the last few months. The possible liability of at least € 20 million or 4% of the global group turnover, whichever is more extensive, has not yet been exhausted, but 8-digit penalties have been overtaken several times during the year. The H&M online shop’s operating company from Germany tops this list with € 35 million, followed by TIM from Italy, British Airways, and Marriott International, Inc from Great Britain, with each remaining € 20 million.
Why are there so many high penalities, is there anything in common between these different cases?
H&M and TIM collected and evaluated data in a way not compatible with data protection regulations. H&M, for example, collected systematic data about the personal life circumstances of some of the employees in their Nuremberg service center and used this information for employment decisions. These kinds of violations are a management problem. Every organization has to ensure that procedures that systematically violate data privacy standards are not established. The intent explains the high of the penalties in these two cases.
British Airways and Marriot International Inc. were both victims of data breaches as a result of cybersecurity incidents. The penalties are both based on insufficient technical and organizational measures to ensure personally identifiable information security. Both companies should better have invested the over € 20 million of penalties into cybersecurity programs. Suppose an organization needs to handle personally identifiable information at each business transaction, as required for hotels and airlines. In that case, these organizations should pay very close attention to the security of the personally identifiable information they collect. In the case of security, paying attention always means a continuous process, not a one-time action. Attackers evolve, new vulnerabilities are exposed every day, and continuously new threat actors are entering the stage.
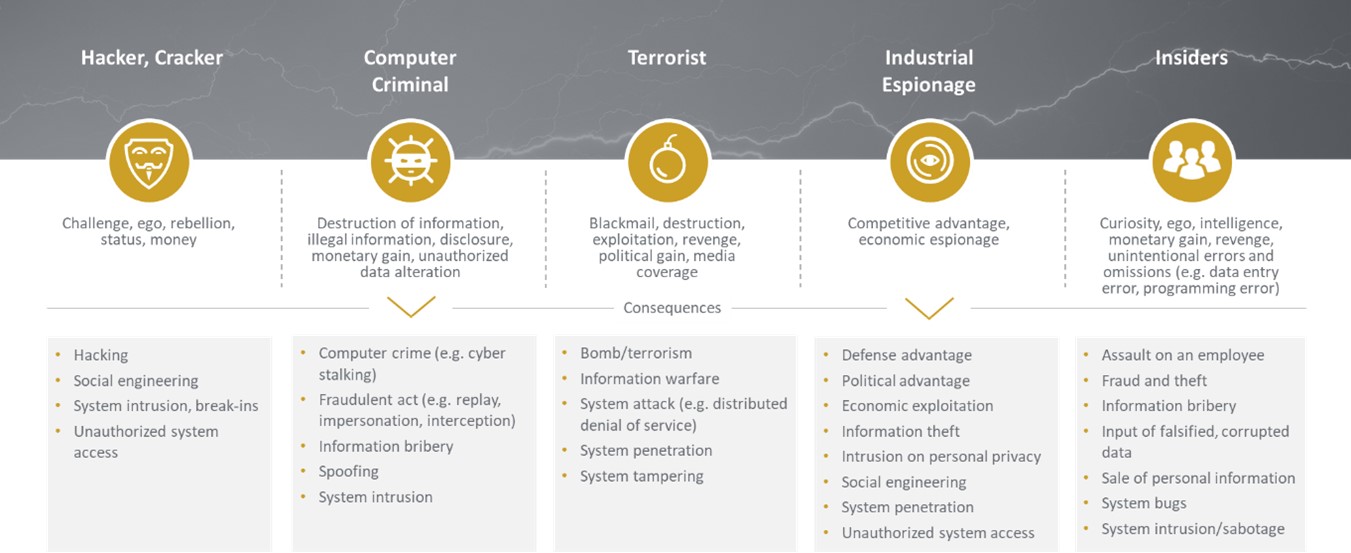
Figure 1: Typical threat-actors, their motivation, and the consequences
In the early days of computer security, we had only to face hackers and crackers searching for reputation and new challenges. In a second phase, the advancing digitalization produced the malicious insider as a unique and highly dangerous treat-actor. Insiders typically search for monetary gain or revenge. In addition to the threat of industrial espionage and terrorism, common criminals are now the biggest problem in information security. Just as information theft and sabotage of business processes have evolved into a business model, the protection of information and business processes must become an essential part of any business model that collects, processes, and stores personally identifiable information. If you have any doubt you are doing the right to ensure your customer’s data, contact us. Our mission is: “Getting digital done – securely.”


Recent Comments