A couple of years ago, almost every IT system was a dedicated standalone solution with only one purpose . Calculating the best path for the first NASA moon mission or creating a digital weather forecast for the first time in history. All those systems did not need to communicate to other IT systems because they combined all required capabilities in themselves.
Unlike today where every system from the smartphone in our pocket to the ERP Systems of the biggest internationally acting companies like Google and Amazon is connected to a variety of other IT systems to enable close collaboration with suppliers, customers, employees, or to enable your smartphone to check a local weather report.
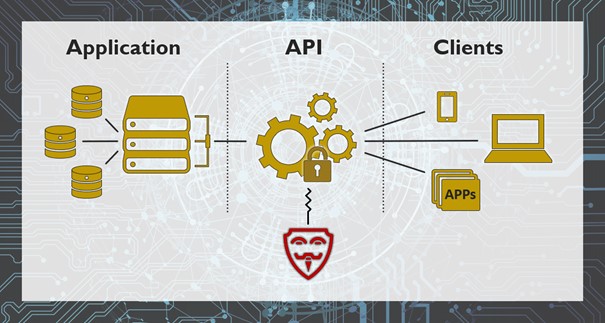
Figure 1: Illustration API Security
To make such inter-system communication possible, we need an API – an Application Programming Interface that allows one IT system to interact automatically with another one in a well-defined way without human intervention.
But what about the security of those interfaces if they are all well-defined? The problem is that APIs were often not in the focus of cybersecurity measures as they were just implemented to connect two existing systems as quickly as possible, not considering possible ways to attack this communication line. Often no actions are taken to document such sensitive system modifications leading to parts of the API deprecating or test modifications making it into the production system. Suddenly, without anyone noticing, the API is, for example, able to export sensitive production data into the internet.
Therefore, APIs are often the first target to investigate for potential attacks. Their inherent complexity leads to a multitude of creative ways to exploit the API’s weaknesses, reaching from basic .
To prevent such attacks, there is a range of best practices that should be implemented. API Security needs to be a priority right from the start when developing or maintaining software. It is essential to get rid of the “someone else’s problem”-mentality. Furthermore, it is key to manage and document all APIs not just when they are developed but during their whole lifecycle . Principles like encrypted traffic, least privilege, validate input, rate-limiting and application firewalls round out the mix of considerations, to tackle the issue of API security.
Getting API Security right can be a complex topic. If you need a reliable partner to secure your APIs, contact us at info@ginkgo-cybersec.com. Our mission at Ginkgo is: “Getting digital done – securely.”


Recent Comments